Do not assume security is extensive enough to protect your critical data and processes. Take a layered security approach using different tactics to establish best practices for protecting network data
Almost daily, the headlines tout the latest data breach that puts company proprietary information in jeopardy. To avoid such situations, many enterprises enforce different security measures to protect data from known and unknown risks. In addition to protecting information stored in the corporate infrastructure, businesses must also consider the data transmitted over any network. Attacks on wireless sensor and control networks can result in lost data and unintended system operations that cause production loss or safety issues.
Even information that seems to pose little risk if not secured can impact operations. A simple tank level reading may, by itself, seem unnecessary to protect. However, if an outsider tampers with data and changes the values, a false reading could shut down operations or even cause a spill. Therefore, both sensor readings and commands must remain valid. For example, a bogus “high” tank level alert sent by an attacker could trigger a production shutdown. Conversely, an erroneous “low” tank level warning could lead to tank overflow and spill.
As wireless sensing and control networks are more prominently used to monitor and control a wide range of assets in industries as diverse as oil and gas, agriculture, water treatment, food processing and transportation, network security is essential to ensure the authenticity, confidentiality and integrity of data as they pass from device to device. Using different security measures, companies can ensure data are only read by the intended recipient and remain valid without any content modification from the point of transmission to the point of reception. To validate sensor data passing through different transmission points, layers of protection must safeguard data packets from malicious attackers who could steal and change the contents. While wirelessly transmitting data without integrity checks is risky, many companies still do not implement security protocols to protect their network data.
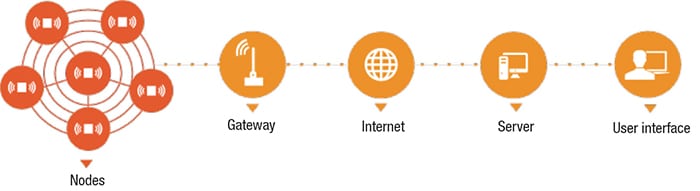
Figure 1. Security checks must protect sensor data as they passes through the wireless remote monitoring and control system. Using data without an integrity check is risky as it can cause unknown actions
Transmitting data wirelessly
Figure 1 outlines a standard configuration of a wireless asset monitoring-and-control system. Nodes extract, and transmit data from sensors via radio transmission to a gateway that serves as the central hub to serve data to a variety of applications. A wireless sensor network can concurrently monitor different assets from a variety of sensors in one network.
For example, in the upstream oil-and-gas market, measurements of level, temperature, vibration, pressure, flow and other parameters can be tied into one network. The gateway of such a network formats sensor data per industry standards (like Modbus) so that programmable logic controllers (PLCs), distributed control systems (DCS), supervisory control and data acquisition systems (SCADA) can process the data. The information is delivered and integrated over a wired digital protocol like Modbus serial (RS485), Modbus over Ethernet (Modbus TCP), Ethernet IP or wirelessly using cell modems or satellite communications.
More than automating data collection, these wireless telemetry systems are capable of managing assets “over the air” (sending an alert that controls a valve), eliminating the use of expensive cabling. Furthermore, the collected data are downloadable into analytics software for asset condition monitoring and predictive diagnostics.
One wireless sensor monitoring-and-control system can employ gateways that accommodate hundreds of transceiver nodes spread out over many square miles. Because of the wide geographic range of the network and critical nature of the processing facilities, security is a must to protect against potential breaches as data pass from point to point. The first line of defense is the sensor network as it packages the data. The second line of defense is the hub (that is, the gateway), where data are served to applications.
Types of data threats
Different types of data intrusions can interrupt a wireless sensor network or create some vulnerability, jeopardizing the reliability and integrity of information moving bi-directionally over the wireless network. A breach of the data moving to and from an asset could cause a problem with the plant or process operations. One common threat or technique to breach a digital communication (wired or wireless) is a replay attack (Figure 2). For instance, a hacker could capture an encrypted message and retransmit it later to the network. This delayed/repeated message can cause potentially serious negative effects throughout the entire operation. For example, repeated transmissions of a low-pressure signal from a vessel could result in the control system not shutting a valve promptly to bring the process to a safe state.
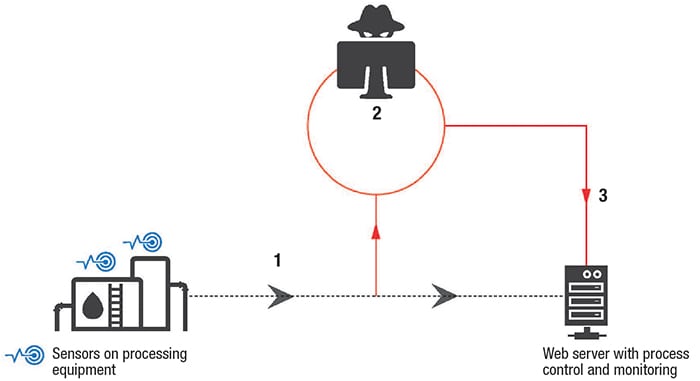
Figure 2. Shown here is an example of a replay attack, which can disrupt operations when messages are intercepted for delayed transmission
Best practices
Companies employing wireless sensor networks, or any digital communication, should use a network security model (NSM) with multiple layers of security, such as encryption, device authentication and replay prevention. Here are some best practices to consider:
AES-128 data encryption. This type of encryption, by the U.S. National Institute of Standards and Technology (NIST), supports a more reliable and secure wireless network within all communication systems because it protects electronic data from intrusion and ensures only designated recipients can read the information. When implemented on low-power sensor devices, it protects against data tampering. The AES-128 works with a CBC-MAC algorithm on encrypted payload data that generates an authentication code sent along with data. If any data are modified, the authentication code becomes invalid as they will not correspond to the payload data. Therefore, the telemetry system will ignore the sent data packet. Only devices with the correct “key” will be able to decrypt the data.
Device authentication.Device authentication is a technique that ensures that nodes within a network pass an integrity check before joining a network. An encrypted, one-time-use token, along with address information, passes from a node to the joining network. The token is decrypted by the gateway (or other nodes already joined on the gateway) using the network key. If the node passes the integrity check and decryption, it will respond with a packet containing the token, address information, and network time. The use of the token stops a rogue network from attempting to absorb joining nodes and preventing them from communicating with their intended network. Additionally, this process allows only authenticated nodes to connect to the network.
Replay prevention. Replay prevention stops a malicious device from resending a message. A common security attack is the capture and re-transmission of a data packet. In replay attacks, the encryption is not broken but encrypted messages are captured and re-transmitted. For example, a message to turn on a relay could be captured and resent at a later time to disrupt operations. In a way, a replay breach can be described as a device analyzing a communication to determine the start and end of a transmission so it can then copy and paste the message ad hoc. Without replay prevention, this message could be resent without the receiving node knowing its delivery was from an attacker.
For example, should an encrypted message “to turn on a relay or change the state of an output” be captured and sent later, operations could be at risk. Replay prevention schemes are typically based on time synchronization of all nodes in the network or message sequence numbers, allowing only fresh messages to be accepted by the network. Many wireless-encryption standards do not protect against this type of attack.
FHSS. Frequency Hopping Spread Spectrum (FHSS) protocol continually changes the radio frequency (RF) of transmissions and receptions to avoid RF interference. Frequency hopping systems typically use a minimum of 50 channels and hop in a random pattern to increase security, as an attacker must synchronize to the frequency channel to receive or transmit a message. If a message is sent on the wrong channel, the network will not receive it.
Who is responsible?
Protection for the wireless sensor network must extend beyond standard information technology (IT) security applied to computer networks and user interfaces. The first line of defense is a wireless technology capable and responsible for protecting its information. Companies must ensure the selection of wireless sensor monitoring and control solutions from vendors that offer multiple layers of protection and not just data encryption (Figure 3).
Data breaches can happen anywhere, even in remote locations unattended by operators for extended periods. Discuss security features with your vendor to ensure that security measures are extensive enough to protect your data network.

Figure 3. Secure commercial systems use firmware, including data encryption and device authentication, on their wireless remote-monitoring products for a more reliable and secure wireless network infrastructure
Concluding remarks
Users of wireless sensor networks should not overlook the risks of intruders tampering with data that control their production processes. Do not assume security is extensive enough to protect your critical data and processes. Take a layered security approach using different tactics to establish best practices. Consider the type of data and control messages that the wireless sensor network will transmit and evaluate the possible consequences of not properly securing that data. In almost all cases, data breaches or attacks put operations and processes at risk. Even in remote locations that are not readily accessible, threats can be present, often without companies realizing it until experiencing a problem.
Author
 Josh Schadel serves as director of engineering at SignalFire Wireless Telemetry (140 Locke Dr., Suite B Marlborough, MA 01752; Phone: 978-212-2868; Email: josh.schadel@signal-fire.com) and is responsible for new product development. With more than 15 years of experience in high-tech instrumentation, he has a strong background in embedded systems and printed circuit board (PCB) designs as well as sensor networks.
Josh Schadel serves as director of engineering at SignalFire Wireless Telemetry (140 Locke Dr., Suite B Marlborough, MA 01752; Phone: 978-212-2868; Email: josh.schadel@signal-fire.com) and is responsible for new product development. With more than 15 years of experience in high-tech instrumentation, he has a strong background in embedded systems and printed circuit board (PCB) designs as well as sensor networks.