As potential threats continue to make headline news around the world, it is clear that the need for security measures is an ongoing process, and that this process requires vigilance. The chemical process industries (CPI) are considered part of the critical infrastructure in the U.S., and as such are regulated by the U.S. Dept. of Homeland Security (DHS; Washington, D.C.; www.dhs.gov) under the Chemical Facility Anti-Terrorism Standard (CFATS). Already renewed for one year, the standard is again set to expire in October 2010, but all signs are that CFATS is here to stay and the CPI have taken great strides toward compliance.
CFATS implementation
“The chemical industry is well along in implementing the current chemical security regulations, which are rigorous, enforceable and protective of the American public,” says Lawrence Sloan, president and CEO of the Society of Chemical Manufacturers & Affiliates (SOCMA; Washington, D.C.; www.socma.com). At the 2010 Chemical Sector Security Summit and Expo held in July, Sue Armstrong, acting deputy assistant secretary for Infrastructure Protection of the DHS, reported on the progress made with CFATS implementation. At the time of the summit, over 38,000 top-screens had been submitted and reviewed; over 6,000 security vulnerability assessments had been submitted and reviewed; over 3,100 site security plans had been submitted and were in review; and DHS inspectors had made over 244 compliance assistance visits. As of June, almost 5,000 facilities were covered by CFATS with rankings in the top four tiers. Over 4,000 of these facilities were given final tiers and the rest were preliminarily tiered facilities (for more on CFATS, “tiers” and other CFATS-related terms see Chemical Plant Security, Chem. Eng., pp. 21–23, September 2009).
Revisions being considered. Even as compliance moves forward, several aspects of CFATS are under scrutiny by the U.S. Congress. One main issue is a proposed revision to mandate use of inherently safer technology (IST). Other areas of discussion relate to broadening the scope of the standard to include, for example, water-treatment plants. Congress is considering multiple bills in the House of Representatives and Senate to either reauthorize the existing standards for a limited time or to significantly alter them.
In late July, legislation that would make the existing CFATS standard permanent took a step forward with bipartisan support in the Senate Homeland Security and Government Affairs Committee. The legislation would extend the existing CFATS by three years, to October 2013. Both SOCMA and the American Chemistry Council (ACC; Arlington, Va.; www.americanchemistry.com) support this extension of the current standard.
Referring to the recent Senate committee’s actions, Sloan says “We thank Senator Collins for this extension, which gives chemical manufacturers and DHS valuable time in which to continue to strengthen protections against attack and more fully assess the effectiveness of the entire CFATS program.” The next step in the legislative process for this bill is consideration by the full Senate.
Harmonization. While CFATS is the main regulatory agent for CPI security, there are a number of exemption categories under which facilities must comply with other governing bodies. One example is that some facilities fall under the Maritime Transportation Security Act (MTSA) regulations. For some of these facilities, there is concern about how to comply with overlap among various government agencies, and this concern was expressed during a question-and-answer period at the July Chemical Sector Security Summit. This concern is recognized and being addressed by an effort to create multi-agency harmonization through working group initiatives, such as the MTSA/CFATS Harmonization group.
Security experts
Security in the CPI did not start with CFATS. As ACC president and CEO Cal Dooley states, “Since 2001, ACC members have helped lead the way on chemical security, well ahead of government regulation. They have invested more than $8 billion on facility security enhancements under ACC’s Responsible Care Security Code.” Even so, there has been much activity in CPI security recently, mostly due to CFATS and perhaps partly due to the greater visibility and interest given to security and the corresponding increase in available resources.
Ryan Loughin, director of the chemical & energy solutions of ADT Advanced Integration (Norristown, Pa.; www.adtbusiness.com/petrochem) says that “Just in the last 30–60 days there has been a lot of movement from DHS, so there has also been a lot of movement from the CPI,” referring to requests for security system design, awarding of contracts and more. Companies are asking for help in designing their site security plans (SSPs) and then redesigning them when rework is needed as feedback from the DHS is received, explains Loughin.
For CPI facilities seeking help, there are a number of security-expert companies, such as ADT and others, that offer assistance with designing, building and managing security systems. And these companies have developed expertise with CFATS so that they can, for example, specifically address what a facility might do to meet the requirements of the risk-based performance standards (RBPSs) that are established in CFATS. “One of the beautiful things about the RBPSs,” says Michael Saad, senior director consulting services with Huffmaster Crisis Response (Troy, Mich.; www.huffmaster.com), “is that they leave it to the facility to determine how to achieve the level of security performance required. But that is a sword that cuts both ways. It also requires the facility to determine how to create layers of integrated security.” This is where the security experts can help.
Managed services and other trends. At a briefing given on August 10 at Siemens AG’s (Munich, Germany; www.siemens.com) U.S. headquarters for their Security Solutions Business Unit (Buffalo Grove, Ill.; usa.siemens.com/buildingtechnologies), Carey Boethel, vice president and business unit head for Security Solutions, explained two trends that are currently shaping security strategies. The first is a proliferation of physical security information management (PSIM) and command-and-control centers. This refers to command-and-control centers that work toward an efficient information flow during emergency situations to ensure a unified command and intelligent response to threats — a control center at a police department was given as an easy-to-understand example. Formerly, only very large businesses were interested in these centers due to the expense, but more recently that is changing.
The second trend is hosted or managed services. This refers to hiring an outside company — a security expert — to monitor the incoming security data (from video surveillance, for example, but also a wide-range of other information) and initiate actions when needed. As Boethel explains, “Hosted applications once focused on small and medium-sized businesses, but are now entering an enterprise-class phase where large multinational companies are embracing the technology.” In fact, Boethal expects that managed video services industry-wide will have more than a 15% compounded annual growth rate. An interesting conclusion can be drawn from these two trends — the distinction between “high-end” and “low-end” security system users is going away. Large, mid-sized and small facilities are exploring all options for their site security plans.

Phil Atteberry, director of managed security services at Siemens, manages both of Siemens’ remote-monitoring centers in Dallas, Tex. (Figure 1) and Beltsville, Md. He has seen a “huge trend” toward managed services with about an 8% increase from 2007–2010 in third-party security monitoring. Atteberry sheds some light on the reasons for this increase when he says “Before it was a single-alarm system, but now it is more enterprise-based … one focal point can monitor the total situation awareness of the facility.” Advantages of third-party security monitoring include having an expert, who best understands the incoming security data, monitor it; reducing or eliminating the need for onsite monitoring personnel and the associated costs; and reducing the potential that an event might be missed due to a lapse of attention to a video screen, for example, during a long period of inactivity on the screen. Since remote centers monitor a number of sites, there is inherently more activity being monitored and therefore more stimulation to keep personnel attentive.
The increase in requests for remote monitoring is a trend that has been noted by a number of security experts. ADT’s Loughin sees more requests for third-party video and alarm monitoring for their special operations monitoring facility in Aurora, Colo., and cites cost-effectiveness as a strong reason for this movement. Saad also notes that an increase in demand for Huffmaster’s interactive remote-video-monitoring services led Huffmaster to renovate and expand the space and resources devoted to those services.
Securing process control
For the CPI, securing process control systems is a vital part of any security plan. And, the CPI has been very actively involved in leading-edge efforts in cyber security. An example of this is the Roadmap to Secure Control Systems in the Chemical Sector (www.us-cert.gov/control_systems/pdf/ChemSec_Roadmap_First_Edition.pdf), which is a document published in September 2009 that presents a security vision for industrial control systems in the CPI, proposes a comprehensive plan for implementation, and identifies milestones over a ten-year period. Preparation of the roadmap was truly a cooperative effort that included the DHS and a substantial number of volunteers from CPI companies.
Citing the roadmap and other efforts in cyber security standards, Ernest Rakaczky, portfolio manager of control system cyber security for Invensys Operations Management (Plano, Tex.; www.iom.invensys.com) says “In a lot of ways, the chemical sector is leading the way.” Rakaczky stresses the importance of control and IT experts working together toward the common goal of security. He says that typically, firewall technology is changing faster than controller technology. With a core competence in control, Invensys builds its control systems so that they can easily be updated with the latest security systems. This built-in ability to update the control system allows the user to take advantage of the newest technologies without large investments.

Threats to control systems can come from a variety of sources. Firewalls are very effective at preventing intrusion. People with access to the control system, however, are a credible threat, whether through accidental means (such as unwarily using personal devices or USB sticks), or through intentional means (such as by a disgruntled employee for example). “A malicious insider is the tough threat,” says Graham Speake, principal systems architect for Yokogawa Corp. of America’s (Newnan, Ga.; www.yokogawa.com/us) IA Global Strategic Technology Marketing Center in Dallas, Tex. Threats to control systems are “no longer theoretical” says Speake, citing the recently discovered Stuxnet worm that was distinctly targeted to attack a specific control system. “One way to increase security,” says Speake, “is to build more security into products so that no matter how you put them together they are still secure.” Yokogawa says it has taken a step in that direction by developing the world’s first field wireless devices based on the ISA100.11a industrial wireless communications standard (Figure 2).
What makes the Stuxnet worm such big news in the control community is not just that it was deliberately made to attack control systems, but that it is highly sophisticated — enough so that it attacks a previously unkown vulnerability and it wraps libraries to hide PLC programming changes. “The worm is a wake-up call. A lot of operations people and even security decision makers had still been on the page that malware is only an incidental threat to control systems and physical processes, and that sophisticated threats … were not something they had to worry about. All that has changed with Stuxnet,” says Andrew Ginter, chief security office with Industrial Defender, Inc. (Foxboro, Mass.; www.industrialdefender.com).
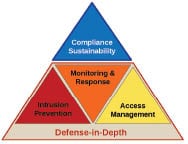
A basic principal of cyber security plans offered by Industrial Defender is Defense-in-Depth (Figure 3), which presumes that no single mode of security mitigation is impenetrable and therefore several layers are needed. The company’s approach includes three major categories including: intrusion prevention, which is applied at network perimeters with a firewall, and within servers and end-point devices via the recently introduced Host Intrusion Prevention System (HIPS); access management, which provides rigorous authentication and authorization before allowing access through the perimeter; and monitoring and response, which integrates intrusion detection, performance monitoring and event management.
Third-party management. An interesting shift is occurring in that more companies are looking for outside security management of not only physical security systems, but also cyber security systems. Ginter explains that while there has been a reluctance to let information out to third parties, companies are getting more comfortable with this through cloud computing and “software as a service”, where computers and functionality are rented. He says that some CPI customers have said that “If you’ve got a good security posture now and you want to take a step up, outsource it.” Their reasoning is that industrial-control-security experts, such as Industrial Defender, understand the system and follow the rules (set up by the user) since that’s what they get paid to do. Industrial Defender has a remote control center at its headquarters in Foxboro, Mass.
Invensys’ Rakaczky says, “One element where there is a big future is managing security. The overall success of security is not [a question of] how many firewalls or security devices I put in, but once I do this, how do I manage it?” He sees a goal to be learning how to address an attack and how to manage it so that a user can work through the attack (and not shut down). And Speake, who fairly recently joined Yokogawa coming from a CPI company, says that with his CPI background, when it comes to managing the security systems he would choose to outsource it. He cautions, however, that you would have to be careful about who does it and where.
A cultural shift
With CFATS implementation well underway, and cooperative working groups, such as those involved with the Roadmap to Secure Control Systems in the Chemical Sector, and those working on standards to improve wireless security, there is a heightened level of awareness about security — both physical and cyber — in the CPI. Most agree that the typical CPI facility has a well-established safety culture where, as Rakaczky puts it “everybody in the plant has a stake in ensuring that everyone is safe.” He says that this type of culture that drives safety is getting started on the security front, and that “training, policies and procedures, and managing everyday activities will have the biggest influence on cyber security.”
Andrew Wray, senior global marketing manager with Honeywell Process Solutions (Phoenix, Ariz.; www.honeywell.com), another leader in expert security systems, has noticed a “cultural shift in a plant environment where everyone feels more a part of security.” Whereas people have previously viewed certain surveillance items, such as video cameras, an intrusion on their privacy, Wray says that now “People believe they have a right to feel secure and safe, and they see video surveillance as a benefit to that end.”